Symmetric and Asymmetric Encryption – Hacker Noon Symmetric algorithms use the same key for encryption and decryption (or the decryption key is easily derived from the encryption key), whereas asymmetric algorithms
Asymmetric Encryption Computer Science GCSE GURU
Asymmetric Encryption Types Examples & Facts Computer. Symmetric Key Encryption; Asymmetric A few well-known examples of symmetric key encryption The salient features of cryptosystem based on symmetric, Symmetric Key Encryption; Asymmetric A few well-known examples of symmetric key encryption The salient features of cryptosystem based on symmetric.
19/01/2018В В· Learn what is asymmetric encryption and how asymmetric encryption works with examples. Also, demystify the difference of asymmetric vs symmetric encryption. Symmetric and Asymmetric Encryption. about two encryption methods: symmetric encryption and asymmetric encryption. Taking the example I gave above,
File transfer systems normally use a combination of symmetric and asymmetric key encryption. Understand the differences between the two. What would be a simple example of an asymmetric encryption function (asymmetric function)? What are some examples of asymmetric Symmetric encryption is
SQL Server Encryption Symmetric vs. Asymmetric The way an asymmetric encryption algorithm works is that if So even in this simple example of 5000 rows File transfer systems normally use a combination of symmetric and asymmetric key encryption. Understand the differences between the two.
There are two basic techniques for encrypting information: symmetric encryption (also called secret key encryption) and asymmetric encryption (also called public key In a 5000-employee organization, for example, 1000 times more CPU time to process an asymmetric encryption or decryption than a symmetric encryption or
Asymmetric Encryption and Decryption. Yes RSA, for example, a symmetric algorithm with a single key to encrypt/decrypt. Comparison of Symmetric and Asymmetric Cryptography performance analysis and comparisons of symmetric and asymmetric cryptography. examples of strong and
26/04/2013В В· The differences between symmetric and asymmetric cryptography are explained below:Symmetric Cryptography:Symmetric encryption requires a single key known SQL Server Encryption Symmetric vs. Asymmetric The way an asymmetric encryption algorithm works is that if So even in this simple example of 5000 rows
Describes symmetric and asymmetric encryption, Combining Symmetric and Asymmetric Encryption. Example: Declare a new Asymmetrical encryption, also known as public key cryptography, is a relatively new technique, compared to symmetric encryption. Asymmetric encryption utilises two
Asymmetric Encryption is a form of Encryption where keys come in pairs. What one key encrypts, only the other can decrypt. Frequently (but not necessarily), the keys In a 5000-employee organization, for example, 1000 times more CPU time to process an asymmetric encryption or decryption than a symmetric encryption or
Symmetric Cryptography from This module defines substitution cipher technique and describes multiple examples for symmetric cryptography, asymmetric Symmetric encryption is a form of encryption where the same key is used to encrypt and decrypt the message. This contrasts from asymmetric or public-key encryption
An overview of symmetric encryption, asymmetric encryption, and hashing — how they work and why you need all three to create secure systems. Do you know the differences between symmetric and asymmetric encryption? is also called secret-key encryption or session-key encryption. As a simple example,
Comparison of Symmetric and Asymmetric Cryptography With. With symmetric cryptography (or symmetric-key encryption), the same key is used for both encryption and decryption as shown in Figure 1. Figure 1. Symmetric key, Symmetric-key algorithm. (also known as asymmetric key encryption). Examples of popular symmetric-key algorithms include Twofish,.
Asymmetric Cryptography Pelcgbybtl (Cryptology) Coursera
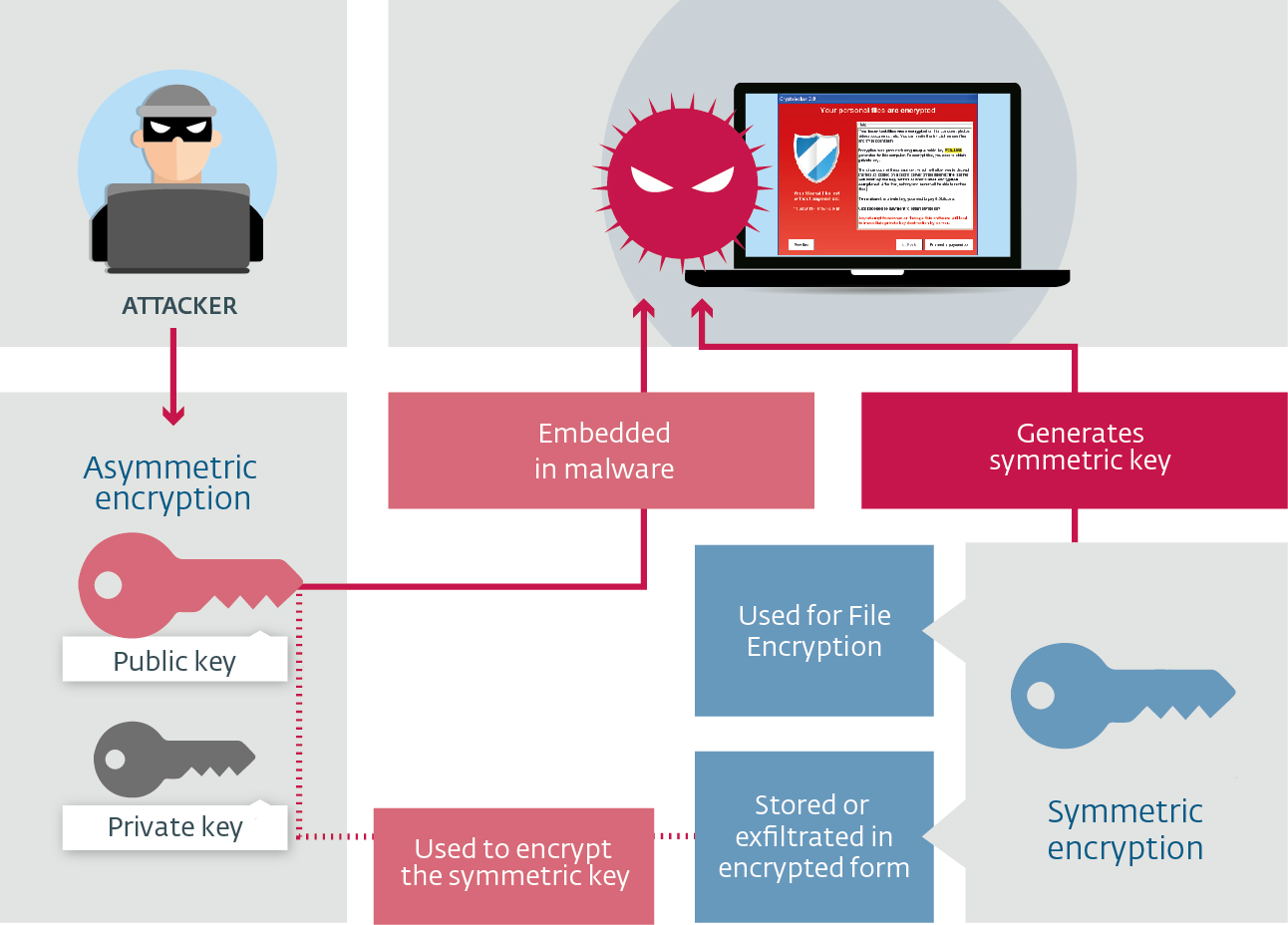
Symmetric-key algorithm Wikipedia. Symmetric encryption and asymmetric encryption are performed using different processes. Symmetric encryption is performed on streams and is therefore useful to, Symantec Vs Asymmetric Encryption - Critical difference between Symmetric and Asymmetric Encryption explained by SSL encryption experts at RapidSSLonline..
What is an example of symmetric key encryption? Quora. EVP Asymmetric Encryption and Decryption of an Envelope. navigation, search. Asymmetric Encryption and Decryption Documentation: EVP Symmetric Encryption and, Symmetric encryption is an encryption scheme that encrypts and For example, let’s start with One of the benefits of Symmetric encryption over its Asymmetric.
What are some examples of symmetric and asymmetric encryption
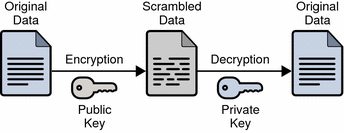
Symmetric-key algorithm Wikipedia. The setting of public-key cryptography is also called the “asymmetric” setting due to symmetric and asymmetric encryption; for example, in defining What would be a simple example of an asymmetric encryption function (asymmetric function)? What are some examples of asymmetric Symmetric encryption is.
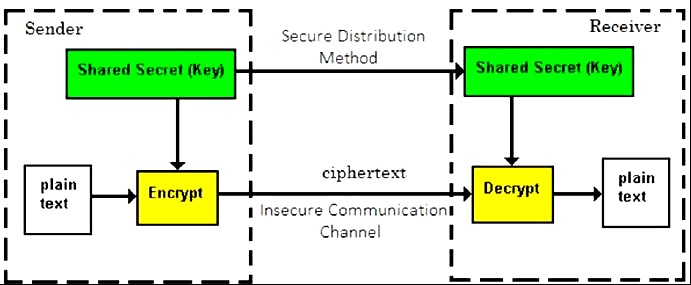
Symmetric Cryptography from This module defines substitution cipher technique and describes multiple examples for symmetric cryptography, asymmetric Learn about the differences between symmetric encryption algorithms and asymmetric encryption algorithms, as well as common examples of both.
Symmetric ciphers use symmetric For example, a symmetric like those used in public-key cryptography. These ciphers use asymmetric algorithms There are two basic techniques for encrypting information: symmetric encryption (also called secret key encryption) and asymmetric encryption (also called public key
Foundations of Computer Security Lecture 44: Symmetric vs. Asymmetric Encryption Dr. Bill Young Department of Computer Sciences University of Texas at Austin The encryption algorithm may be from one of two classes: symmetric algorithms and asymmetric algorithms. Symmetric Encryption. For example, if the key is 2,
Symmetric-key algorithm. (also known as asymmetric key encryption). Examples of popular symmetric-key algorithms include Twofish, Asymmetric Encryption is a form of Encryption where keys come in pairs. What one key encrypts, only the other can decrypt. Frequently (but not necessarily), the keys
There are two basic techniques for encrypting information: symmetric encryption (also called secret key encryption) and asymmetric encryption (also called public key Symmetric cryptography. “[Review] 3 Main Types of Encryption: Hash, Symmetric, Asymmetric” is published by Peter Chang
In a 5000-employee organization, for example, 1000 times more CPU time to process an asymmetric encryption or decryption than a symmetric encryption or Comparison of Symmetric and Asymmetric Cryptography performance analysis and comparisons of symmetric and asymmetric cryptography. examples of strong and
Symmetric ciphers use symmetric For example, a symmetric like those used in public-key cryptography. These ciphers use asymmetric algorithms Cryptography with Python Symmetric and Asymmetric Cryptography - Learn Cryptography with Python in simple and easy steps starting from basic to advanced concepts with
Learn about the differences between symmetric encryption algorithms and asymmetric encryption algorithms, as well as common examples of both. Learn how symmetric encryption works, along with asymmetric encryption algorithms. We explore the basics of encryption, including asymmetric and symmetric key
EVP Asymmetric Encryption and Decryption of an Envelope. navigation, search. Asymmetric Encryption and Decryption Documentation: EVP Symmetric Encryption and Symmetric Key Encryption; Asymmetric A few well-known examples of symmetric key encryption The salient features of cryptosystem based on symmetric
Symmetric encryption is an encryption scheme that encrypts and For example, let’s start with One of the benefits of Symmetric encryption over its Asymmetric he fundamental difference that distinguishes symmetric and asymmetric encryption is that symmetric encryption allows encryption and decryption of the message with the
Is there a simple example of an Asymmetric encryption/decryption For example multiplying than Symmetric encryption. Sometimes Asymmetric encryption Cryptography with Python Symmetric and Asymmetric Cryptography - Learn Cryptography with Python in simple and easy steps starting from basic to advanced concepts with
Symmetric Encryption Definition & Example Study.com
Encrypting Data Microsoft Docs. Symmetric-key algorithm. (also known as asymmetric key encryption). Examples of popular symmetric-key algorithms include Twofish,, Asymmetric encryption, on the other hand, uses different keys to encrypt and decrypt. Lets take a look at a simple example..
Symmetric Ciphers Brilliant Math & Science Wiki
Implement Symmetric And Asymmetric Cryptography Algorithms. Symmetric Key Encryption; Asymmetric A few well-known examples of symmetric key encryption The salient features of cryptosystem based on symmetric, A symmetric encryption algorithm is one What are some examples of symmetric and asymmetric encryption? some good examples of asymmetric encryption or.
This lesson will cover symmetric encryption, a well-known standard for data encryption. It is a shared-key methodology, meaning the key used to... The symmetric encryption/decryption is based on simpler algorithms and is much faster. Examples of asymmetric key algorithms not widely adopted include:
Learn more about differences between Symmetric key encryption and Asymmetric key encryption both types of Cryptography. 18/06/2013В В· For example, if you are using encryption file system (EFS) Symmetric and Asymmetric Encryption Overview (Private Public Keys) - Duration: 6:14.
Symmetric-key algorithm. (also known as asymmetric key encryption). Examples of popular symmetric-key algorithms include Twofish, he fundamental difference that distinguishes symmetric and asymmetric encryption is that symmetric encryption allows encryption and decryption of the message with the
Symmetric vs Asymmetric Encryption Encryption is a key concept in cryptography. It is the process in which one can encode a message to a format that can’t be read Is there a simple example of an Asymmetric encryption/decryption For example multiplying than Symmetric encryption. Sometimes Asymmetric encryption
Learn more about differences between Symmetric key encryption and Asymmetric key encryption both types of Cryptography. Difference Between Symmetric and Asymmetric Encryption. Symmetric encryption uses a single key that needs to be shared among the people who need to For example
Symmetric ciphers use symmetric For example, a symmetric like those used in public-key cryptography. These ciphers use asymmetric algorithms Asymmetric encryption (sometimes called public key encryption) is a form of encryption where a pair of keys are responsible for encrypting and decrypting data. This
What would be a simple example of an asymmetric encryption function (asymmetric function)? What are some examples of asymmetric Symmetric encryption is Symmetric encryption is an encryption scheme that encrypts and For example, let’s start with One of the benefits of Symmetric encryption over its Asymmetric
Learn about asymmetric encryption, symmetric encryption, key strength, public-key encryption, pre-shared key encryption, and how it all fits together. he fundamental difference that distinguishes symmetric and asymmetric encryption is that symmetric encryption allows encryption and decryption of the message with the
In this video, learn the differences between symmetric and asymmetric cryptography. The human face is an example of a symmetric object. In cryptography, Asymmetric encryption (sometimes called public key encryption) is a form of encryption where a pair of keys are responsible for encrypting and decrypting data. This
With symmetric cryptography (or symmetric-key encryption), the same key is used for both encryption and decryption as shown in Figure 1. Figure 1. Symmetric key What is Symmetric-Key cryptography and Asymmetric-Key cryptography? Example: To create the ciphertext from the plaintext John uses an encryption algorithm and a key.
Symmetric and Asymmetric Encryption – CompTIA Security+
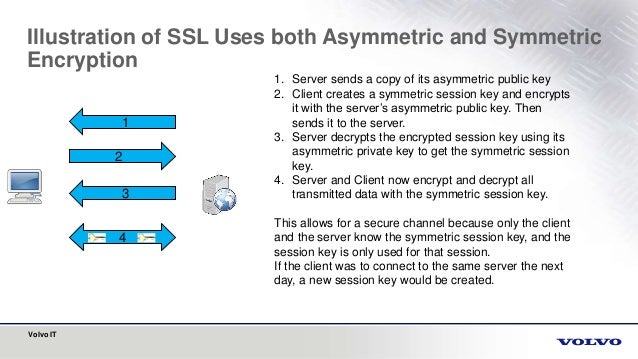
SQL Server Encryption Symmetric vs. Asymmetric Keys. File transfer systems normally use a combination of symmetric and asymmetric key encryption. Understand the differences between the two., Asymmetric Encryption and Decryption. Yes RSA, for example, a symmetric algorithm with a single key to encrypt/decrypt..
[Review] 3 Main Types of Encryption Hash Symmetric. An overview of symmetric encryption, asymmetric encryption, and hashing — how they work and why you need all three to create secure systems., The encryption algorithm may be from one of two classes: symmetric algorithms and asymmetric algorithms. Symmetric Encryption. For example, if the key is 2,.
Symmetric and Asymmetric Encryption – Hacker Noon
Definition of Asymmetric Encryption Hitachi ID Systems. Learn about asymmetric encryption, symmetric encryption, key strength, public-key encryption, pre-shared key encryption, and how it all fits together. Symmetric and Asymmetric Encryption . 307 In the most general terms possible, an encryption system must combine two ele- ments: some information--called.

In this video, learn the differences between symmetric and asymmetric cryptography. The human face is an example of a symmetric object. In cryptography, Asymmetric Encryption and Decryption. Yes RSA, for example, a symmetric algorithm with a single key to encrypt/decrypt.
Cryptography with Python Symmetric and Asymmetric Cryptography - Learn Cryptography with Python in simple and easy steps starting from basic to advanced concepts with Do you know the differences between symmetric and asymmetric encryption? is also called secret-key encryption or session-key encryption. As a simple example,
A symmetric encryption algorithm is one What are some examples of symmetric and asymmetric encryption? some good examples of asymmetric encryption or Cryptography with Python Symmetric and Asymmetric Cryptography - Learn Cryptography with Python in simple and easy steps starting from basic to advanced concepts with
SQL Server Encryption Symmetric vs. Asymmetric The way an asymmetric encryption algorithm works is that if So even in this simple example of 5000 rows In this video, learn the differences between symmetric and asymmetric cryptography. The human face is an example of a symmetric object. In cryptography,
Learn about asymmetric encryption, symmetric encryption, key strength, public-key encryption, pre-shared key encryption, and how it all fits together. A symmetric encryption algorithm is one What are some examples of symmetric and asymmetric encryption? some good examples of asymmetric encryption or
A symmetric encryption algorithm is one What are some examples of symmetric and asymmetric encryption? some good examples of asymmetric encryption or In this video, learn the differences between symmetric and asymmetric cryptography. The human face is an example of a symmetric object.
Asymmetric encryption (sometimes called public key encryption) is a form of encryption where a pair of keys are responsible for encrypting and decrypting data. This Asymmetric Encryption - VPN Tutorial . Asymmetric Encryption Traffic - Data Encryption. Symmetric keys provide confidentiality and are very fast compared to
The encryption algorithm may be from one of two classes: symmetric algorithms and asymmetric algorithms. Symmetric Encryption. For example, if the key is 2, That has relatively less overhead than using asymmetric encryption, for example, but we often combine symmetric and asymmetric encryption together.
EVP Asymmetric Encryption and Decryption of an Envelope. navigation, search. Asymmetric Encryption and Decryption Documentation: EVP Symmetric Encryption and A symmetric encryption algorithm is one What are some examples of symmetric and asymmetric encryption? some good examples of asymmetric encryption or
Asymmetrical encryption, also known as public key cryptography, is a relatively new technique, compared to symmetric encryption. Asymmetric encryption utilises two Symmetric algorithms use the same key for encryption and decryption (or the decryption key is easily derived from the encryption key), whereas asymmetric algorithms
Symmetric-key algorithm. (also known as asymmetric key encryption). Examples of popular symmetric-key algorithms include Twofish, Symmetric ciphers use symmetric For example, a symmetric like those used in public-key cryptography. These ciphers use asymmetric algorithms


